As more and more businesses are transitioning towards cloud-based solutions, tools like Pip are becoming increasingly popular for project management and collaboration. However, using Pip behind a firewall can be challenging without proper authorization. In this article, we’ll provide you with some valuable guidelines to help you authorize URLs for using Pip behind a firewall without any hiccups.
Are you tired of dealing with connection errors when trying to access Pip behind a firewall? Well, you’re not alone! Firewall restrictions can be frustrating, but fortunately, there are effective ways to overcome them. By authorizing the appropriate URLs, you can ensure smooth access to Pip while maintaining robust security measures.
If you’re unsure about how to authorize URLs for using Pip behind a firewall, don’t worry, our guidelines will walk you through it step-by-step. Whether you’re an IT specialist or a non-technical user, our easy-to-understand instructions will help you achieve your goal quickly and efficiently.
So, if you want to maximize the benefits of Pip in your organization, it’s vital to learn how to authorize URLs for using it behind a firewall. With our comprehensive guidelines and expert advice, you’ll be able to do just that. Read on to find out all you need to know about this critical process and start enjoying seamless access to Pip today!
“What Url Should I Authorize To Use Pip Behind A Firewall?” ~ bbaz
Comparison Article: Authorizing URL for Using Pip Behind Firewall – Guidelines
Introduction
Pip is a widely-used tool in Python programming language used for managing packages, installing and upgrading python libraries. Using pip requires internet connectivity, and if you are using pip behind a firewall, it may prevent pip from accessing the required resources. In this article, we will discuss the guidelines for authorizing the URL for using pip behind the firewall.
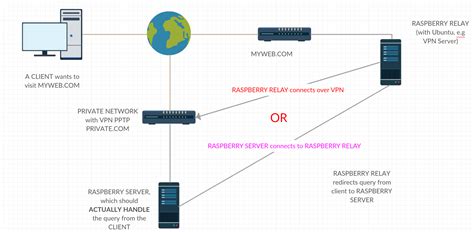
Pip and Firewall
Pip is an online repository where you can find many python libraries. However, firewalls can block the URLs used by pip to access these resources. It is therefore essential to authorize some URLs to ensure proper working of pip while behind the firewall.
Guidelines to Authorize URLs
There are three essential steps to authorize URLs and use pip behind a firewall:
- Check for proxy settings
- Add proxy settings to pip configuration
- Authenticate the URLs
1. Check for proxy settings
If you are behind a firewall, you may be using a proxy server to access the internet. You can verify the proxy settings and make sure that they are correctly set up.
2. Add proxy settings to pip configuration
To add proxy settings to pip, you can set environment variables or modify the pip configuration file. You can use the command-line option –proxy while using pip to install any packages.
3. Authenticate the URLs
After adding the proxy settings to pip, you need to authenticate the URLs used by pip to access the resources. The simplest way to achieve this is by adding the URLs to your company’s allowed whitelist.
Comparison of Methods
There are different methods to authorize URLs for using pip behind a firewall, and we have listed a few popular ones below:
| Method | Pros | Cons |
|---|---|---|
| Whitelisting | Simple and effective solution | May require update due to changes in the URLs |
| VPN Connection | Unlocks access to all online resources and services | Expensive and challenging to configure |
| HTTP Connect Proxy | Can work with any firewall | Does not work with HTTPS connections |
Conclusion
Authorizing URLs is a necessary step if you want to use pip while behind a firewall. Whitelisting is the simplest and most effective method; however, it may require updates due to changes in URLs. Other methods, such as VPN connection and HTTP connect proxy, provide greater flexibility but can be expensive or have some limitations. By following the guidelines discussed in this article, you can quickly set up pip and use it to install python libraries as required.
Thank you for taking the time to read through our comprehensive guidelines on how to authorize URL for using Pip behind a firewall. We hope this article has been informative and has provided you with an in-depth understanding of what it takes to configure your proxy settings and authorize your URLs for pip installation behind a firewall.
With our step-by-step guide, we are confident that you will be able to easily navigate the process and mitigate any possible issues that may arise when installing packages with pip. We understand that configuring proxy settings and authorizing URLs can be complex, which is why we have broken down the process into simple, easy-to-understand steps.
If you have any further questions or would like more information about this topic, please feel free to reach out to us. Our team is always here to help you with any issues you may encounter while configuring your proxy settings and authorizing URLs for pip installation behind a firewall. Thank you once again for visiting our blog and we look forward to hearing from you soon!
Here are some common questions people ask about Authorizing URL for Using Pip Behind Firewall: Guidelines:
- What is an Authorizing URL?
- Why do I need to authorize an URL for using Pip behind a firewall?
- How do I find the Authorizing URL?
- How do I authorize an URL for using Pip behind a firewall?
- Are there any security risks associated with authorizing an URL for using Pip behind a firewall?
An Authorizing URL is a specific URL that allows access to a secured network or application. In the context of using Pip behind a firewall, an Authorizing URL is required in order to download packages from the internet.
If you are using Pip behind a firewall, your network may have restrictions in place that prevent you from directly downloading packages from the internet. By authorizing a specific URL, you are telling your network to allow access to that URL so that you can download packages.
The Authorizing URL will depend on your specific network and firewall settings. You may need to contact your network administrator or IT department to obtain the necessary information.
The steps for authorizing an URL will depend on your specific network and firewall settings. Generally, you will need to access your firewall settings and add the Authorizing URL to the list of allowed sites or exceptions. Again, you may need to consult with your network administrator or IT department for guidance.
There is always a risk when allowing access to external URLs, as it could potentially expose your network to malicious activity. However, by carefully selecting and authorizing only known and trusted URLs, you can minimize this risk.