Detection of Virus Patterns in Emails
Description of Drawback Assertion
The detection of unknown viruses is past the potential of many present virus detection approaches. The target of the project is to develop a prototype system, that can detect the virus which unfold through e mail which haven’t any signatures i.e new and deadly to in the present day’s web neighborhood by utilizing proactive customization of system behaviors at e mail server. This project additionally goals to search out the signature of the newly discovered virus (virus having no signature) to assist curb the unfold of virus at its juvenile section.
Scope of Definition
The harm brought on by pc viruses is extra critical than ever in in the present day’s society,
the place private communication, company enterprise, and social infrastructures closely rely on pc networks.
Sadly, e mail attachments have turn into a preferred methodology of spreading malicious codes over the community. It has result in the rise of anti-virus trade and it’s now nearly compulsory for us to have anti-virus packages on private computer systems and/or e mail servers. But we preserve listening to reviews on new viruses and warnings that now we have to replace sample information to keep away from an infection and additional unfold.
The primary purpose is that present anti-virus packages depend on byte-to-byte comparability between information, the place binary strings taken from beforehand captured viruses are used as distinctive signatures. Since a file is acknowledged as a virus provided that it incorporates matching signatures within the sample file, it’s unimaginable to detect beforehand unknown viruses.
This project goals to deal with the issue by operating suspicious packages in a digital remoted & monitored pc setting. The monitored sources within the setting are these that are widespread to virus for spreading itself (like handle ebook and many others). This project additional go forward to extract the signature of newly discovered virus to assist the web neighborhood to curb it.
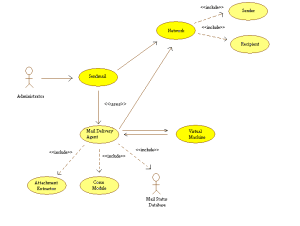
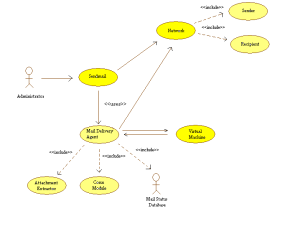
Structure Of Our Proposed Answer
Detection of Virus Patterns Implementation
The prototype prevents e-mail containing new and unknown outbreak viruses from spreading to unsuspecting customers, working with SMTP-based e-mail server to:
- Intercept e-mail on the community edge.
- Execute and monitor the e-mail in a safe, digital setting, and
- Quarantine any e-mail exhibiting malicious habits earlier than supply to the goal consumer.
The above talked about steps are carried out as follows:
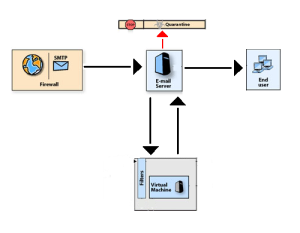
Stage 1:
When the e-mail with attachments arrives on the e-mail server it’s delivered to the mail content material filtering device which extracts the attachments and transports it to the digital machine.
Stage 2:
The attachment is executed & monitored within the safe remoted setting of digital machine operating on the identical host. The malicious actions is intercepted by hooking the varied sources that virus might infect or use to unfold it impact.
Stage 3:
As soon as the malicious exercise is detected within the digital machine it’s reported again to the mail server which then quarantines the e-mail containing the involved attachment and than tries to extract signature for the scanner antivirus so subsequent time it may be caught with out having must test its habits.
Key advantages are as follows
- Executes e-mail and attachments in a digital setting on the community edge, earlier than reaching the goal consumer.
- Observes the tried habits of suspect e-mail to find out its intent
- Quarantines e-mail demonstrating suspicious or malicious habits
- Allows quarantined e-mails to be analyzed and cleaned by an administrator for future supply.
{Hardware} Requirement
Linux 9 with a minimal configuration as follows
- Processor : P IV 1.5 GHz
- RAM : 256 MB
- Onerous disk : 40 GB
- Monitor : 14 inch SVGA shade
- Peripherals : Mouse, 101 key board, 3.5 inch floppy drive, 32X CD-ROM drive.
- Utilities : SMTP.
Workstations with a minimal configuration as follows
- Processor : P III – 800 MHz or equal
- RAM : 128 MB
- Onerous disk : 10 GB
- Monitor : 14 inch SVGA shade
- Peripherals : Mouse, 101 key board
Software program Requirement
- Linux (9 or above ) , Home windows X P.
- VMware.
.
Supply projectgeek.com