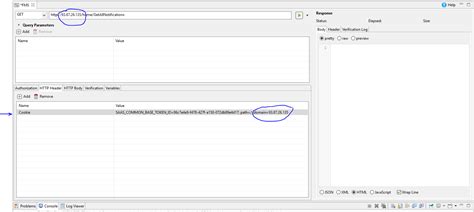
Are you concerned about the security of your website’s login system? Do you want to ensure that only authorized users can access your site and its sensitive information? If so, then you need to consider maximizing security by passing cookies for login authentication.
Cookies are small data files that websites store on a user’s device when they visit the site. These cookies can contain information that helps the site identify the user and their preferences for future visits. When it comes to login authentication, cookies can be used to verify that a user is who they claim to be.
By passing cookies for login authentication, you can reduce the risk of unauthorized access to your site. This method provides an additional layer of security beyond the traditional username and password system. With cookies in place, even if a hacker manages to steal a user’s login information, they won’t be able to access the site without the corresponding cookie.
If you’re serious about keeping your site secure, then you don’t want to miss this article on maximizing security through cookie-based login authentication. We’ll walk you through the process of setting up this system step-by-step so that you can rest easy knowing that your site is protected from unauthorized access.
“Passing Cookies While Logging In” ~ bbaz
Introduction
Security in web applications is a major concern for developers. Login authentication is a common and widely used method to ensure the security of web applications. One way to increase the security of login authentication is by using cookies. This article will explore how passing cookies can maximize web application security and compare it with other methods.
What are Cookies?
Cookies are small text files that are stored on the user’s device by the web server. Cookies can store information about the user session, including login credentials. Cookies can be managed through JavaScript or server-side programming languages, like PHP or Java.
Passing Cookies for Login Authentication
Passing cookies for login authentication involves storing user authentication data in cookies. Once the user logs in, the server generates a unique token and stores it in a cookie. The server then checks the token on every request from the user to verify the user’s identity. If the token is valid, the server allows the user access to the protected resources.
Advantages of Passing Cookies for Login Authentication
- Efficient: Passing cookies for login authentication is a quick and efficient way to verify user credentials as it reduces the need to check on the server’s database on every request.
- Secure: Cookies are encrypted and stored on the user’s device preventing any unauthorized access.
- Scalable: Cookies work well with multiple servers, and it does not matter which server receives the request, as long as they share the same cookie data.
Disadvantages of Passing Cookies for Login Authentication
- Cookie Theft: Hackers can steal authentication data from cookies using methods like cross-site-scripting (XSS) and CSRF (Cross-site Request Forgery).
- Expiry Time: Cookies have an expiry time, and users must log in again to renew it. If the user fails to renew their cookie within the time limit, they will be logged out automatically.
Comparison: Passing Cookies vs. Other Authentication methods
There are several methods for login authentication other than passing cookies. The comparison table below shows how passing cookies compares to other methods.
| Passing Cookies | Token-based Authentication | OAuth | |
|---|---|---|---|
| Security | Secure | Secure | Secure |
| Scalability | Scalable | Scalable | Scalable |
| Efficiency | Efficient | Efficient | Inefficient |
| Easy to Implement | Easy | Difficult | Moderate |
| Authentication Expiry Time | Has an expiry time | Does not have an expiry time | Does not have an expiry time |
| Token Management | Done on the server-side | Done on the server-side | Done on both server-side and client-side |
Opinion
In conclusion, passing cookies for login authentication is a secure and efficient method, but it has its disadvantages. However, compared to other authentication methods, passing cookies is easier to implement, scalable, and efficient. Token-based authentication and OAuth are also secure, but they are harder to implement and not as efficient. It is essential to understand the pros and cons of each method and choose the right method based on the application’s requirements and its security concerns.
Thank you for taking the time to read our article on maximizing security when it comes to passing cookies for login authentication. We hope that you have gained some valuable insights into the importance of keeping your login information as secure as possible, and the potential risks associated with not doing so.
Remember that while cookies can be a convenient way to authenticate your login details and keep you logged in across sessions, they can also be vulnerable to attacks if left unchecked. It is crucial to ensure that you are using the latest security measures to protect your sensitive data and prevent unauthorized access to your account.
If you have any questions or concerns about maximizing your security in this regard, please do not hesitate to reach out to us for further guidance. Your online security is our top priority, and we are always here to help you stay safe and secure in the digital world.
Here are some common questions that people also ask about maximizing security when passing cookies for login authentication:
-
What are cookies and how are they used for authentication?
Cookies are small text files that are stored on a user’s computer or device when they visit a website. They contain information about the user’s preferences, browsing history, and login credentials. When a user logs in to a website, a cookie is created that contains a unique identifier that is used to authenticate the user on subsequent visits.
-
How can I ensure that my cookies are secure?
There are several steps you can take to maximize the security of your cookies, including:
- Using HTTPS to encrypt all data transmitted between the user’s device and your server
- Using a secure session ID to prevent session hijacking
- Setting the secure and httpOnly flags on your cookies to prevent cross-site scripting attacks
- Implementing strong password policies and two-factor authentication to prevent unauthorized access
-
What are the risks of passing cookies for authentication?
The main risk of passing cookies for authentication is that they can be intercepted or stolen by attackers, who can then use them to gain unauthorized access to the user’s account. This is known as session hijacking. Other risks include cross-site scripting attacks, where an attacker injects malicious code into a web page to steal the user’s cookies, and cross-site request forgery attacks, where an attacker tricks the user into performing actions on their behalf.
-
What are some best practices for passing cookies for authentication?
Some best practices for passing cookies for authentication include:
- Using secure cookies that are encrypted and have a limited lifespan
- Implementing a logout button or link that clears the user’s cookies and session data
- Regularly monitoring your server logs for suspicious activity and unauthorized access attempts
- Keeping your software and security protocols up to date to minimize vulnerabilities
-
What should I do if I suspect that my cookies have been compromised?
If you suspect that your cookies have been compromised, you should immediately change your password and enable two-factor authentication if possible. You should also contact the website’s support team to report the incident and ask for assistance in securing your account. Additionally, you may want to consider using a password manager and regularly monitoring your credit report for signs of identity theft.