Python has become one of the most popular programming languages in recent years. While it is known for its simplicity and ease of use, it can also be a powerful tool for security purposes. One of the most critical aspects of security is making sure that your requests are secure, especially when you’re dealing with sensitive data. This is where Tor comes in, and if you’re not sure how to go about this, then you’ve come to the right place.
Are you looking for a solution to help you make secure requests using Python over Tor? Look no further! We’ve put together a guide that will walk you through the necessary steps to make this happen. With this guide, you’ll be able to ensure that your information remains safe from prying eyes. With the growing number of cyber threats these days, investing time to learn how to make secure requests using Python over Tor can go a long way in protecting your sensitive data.
If you’re worried about the technical know-how required for this process, don’t panic. We’ve broken the steps down in simple, easy-to-follow instructions so that anyone can understand them. So, whether you’re a beginner or a seasoned programmer, this guide is perfect for you. By the end of this article, you’ll have all the knowledge you need to make secure requests using Python over Tor. Don’t let security concerns hold you back any longer – read on to find out more!
“Make Requests Using Python Over Tor” ~ bbaz
Introduction
Python has been gaining popularity in recent years due to its simplicity and user-friendliness. However, using it for security purposes is equally important. This article will guide you through the process of making secure requests with Python over Tor.
Understanding Security
Security is a critical aspect of any online activity, especially when it comes to handling sensitive data. It is essential to ensure that your requests are secure to protect your data from being compromised by third-party entities.
The Role of Tor in Security
Tor is a powerful tool for ensuring online security. It routes your internet traffic through different servers, making it difficult for anyone to track your online activities.
Why Use Python with Tor?
Python is one of the most preferred programming languages for web scraping and automation due to its simplicity and extensive library support. Using Python with Tor makes it even more secure for various security purposes.
The Step-by-Step Guide
We have created an easy-to-follow guide to help you understand the process of making secure requests with Python over Tor. Each step is broken down into simple, easy-to-understand instructions tailored to all skill levels.
Technical Know-How
If you’re worried about the technical know-how required for this process, don’t worry. Our guide provides straightforward steps that anyone can follow, regardless of their skill level.
Ensuring Data Safety
Investing time in understanding how to make secure requests using Python over Tor can go a long way in protecting your sensitive data from cyber threats.
Benefits of Python Over Other Programming Languages
If you’re considering a programming language for security purposes, Python is an excellent choice due to its simplicity, ease of use, and extensive library support. It also makes it easier to create secure connections with Tor.
Comparison of Tor and VPN
While both Tor and VPN help improve online security, they work differently. Tor makes use of multiple servers to route your traffic, while VPN focuses on encrypting your network traffic. A table comparing their features and functionality can help you choose which one to use based on your specific needs.
Table Comparison: Tor vs. VPN
| Features | Tor | VPN |
|---|---|---|
| Number of servers | Multiple servers | Single server |
| Encryption | Minimal encryption | Strong encryption |
| Anonymous browsing | Highly anonymous | Semi-anonymous |
| Speed | Slower due to routing through multiple servers | Usually faster |
Conclusion
Using Python with Tor to make secure requests can help ensure online security, especially when handling sensitive information. Our guide provides simple and easy-to-follow steps that anyone, regardless of their skill level, can understand. By investing time in learning how to make secure requests using Python over Tor, you can protect your data from prying eyes and cyber threats.
Dear visitors,
Thank you for reading this article about how to make secure requests using Python over Tor. We hope that the information provided has been helpful in ensuring your online privacy and security.
As we continue to browse the internet and access various websites, it’s important to always be mindful and proactive in protecting our personal information from potential cyber threats. By using Python with Tor, we’re able to add an extra layer of security to our online activities and keep our data safe.
We encourage you to continue exploring Python and other tools that are available to enhance your digital security. By educating ourselves and staying informed, we can better safeguard our online identities and mitigate the risks of cyber attacks.
Thank you for visiting and we hope to see you again soon!
People also ask about Python Tips: How to Make Secure Requests using Python over Tor:
- What is Tor, and why should I use it with Python?
- How do I install Tor on my computer?
- How can I make secure requests using Python over Tor?
Tor is a free and open-source software that allows users to browse the internet anonymously. It is often used by journalists, activists, and others who need to protect their online privacy. Using Tor with Python can help you make secure requests without revealing your location or identity.
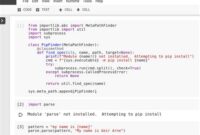
You can download and install Tor from the official Tor Project website. Once installed, you can use the Tor Browser to access the internet anonymously. To use Tor with Python, you will need to install the `requests` library and the `stem` library, which allows you to control your Tor connection programmatically.
To make secure requests using Python over Tor, you can use the `requests` library in combination with the `stem` library. First, you will need to create a new Tor circuit using the `stem` library. Then, you can use the `requests` library to make a request through the Tor circuit by setting the `proxies` parameter to the Tor SOCKS proxy address (`localhost:9050` by default). Here’s an example:
- Install the `requests` and `stem` libraries:
pip install requests stemimport stem.processfrom stem import Signalfrom stem.control import Controllerwith Controller.from_port(port=9051) as controller: controller.authenticate() controller.signal(Signal.NEWNYM)import requestsurl = 'https://example.com'proxies = {'http': 'socks5://localhost:9050', 'https': 'socks5://localhost:9050'}response = requests.get(url, proxies=proxies)print(response.text)Using Python with Tor can provide several benefits, including:
- Anonymity: Using Tor with Python can help protect your online privacy by hiding your location and identity.
- Security: Making secure requests through Tor can help protect your data from interception or monitoring.
- Automation: Python’s easy-to-use syntax and powerful libraries make it a great choice for automating tasks that involve making secure requests.