Are you struggling to safely evaluate simple string equations in your Python code? Look no further! We have expert techniques that will help you avoid common pitfalls and ensure your code runs smoothly.
Whether you’re a beginner or an experienced Python programmer, it’s important to understand the potential risks of evaluating user-generated equations. Our tips will equip you with the knowledge and tools to safely handle string equations and prevent any security vulnerabilities in your code.
So, if you want to ensure your Python code is efficient, secure, and error-free when handling string equations, this article is a must-read for you! Learn from our expert tips and techniques to enhance your Python programming skills today. Don’t miss out on this opportunity to become a more proficient Python programmer!
“Safely Evaluate Simple String Equation” ~ bbaz
Introduction
Python programming language is widely used in various fields, including scientific computing, web development, and artificial intelligence. However, evaluating user-generated equations can pose a security risk for your code. This article aims to provide expert tips and techniques to help you evaluate simple string equations safely.
The Risks of Evaluating User-Generated Equations
When you evaluate user-generated equations, you can face potential security vulnerabilities in your code. For instance, malicious actors can inject harmful code through the input fields to bypass security measures, gain unauthorized access or execute arbitrary code. Therefore, it’s crucial to handle string equations with care.
Basic Evaluation of Simple String Equations
To evaluate string equations safely, you can use Python’s built-in function eval(). It evaluates a given expression and returns its result. However, using eval() without adequate safeguards can lead to a security breach. You can mitigate this risk by sanitizing the user’s input, validating the expression’s structure, and restricting certain keywords or operators.
Expert Techniques to Handle String Equations Safely
There are several expert techniques you can use to handle string equations securely in your Python code. Here are some of them:
Use a Parser Module
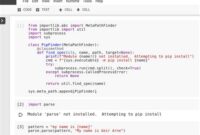
You can use a parser module like ast or pyparsing to parse the string equation into an abstract syntax tree (AST) and validate its structure.
Sanitize Input
Sanitizing input means removing any potentially harmful characters or expressions from the user’s input before evaluating the equation. You can use regular expressions or a whitelist approach to filter out unwanted characters or mathematical functions.
Restrict Keywords or Operators
You can restrict certain keywords or operators from being executed in the string equation. For example, you can disable access to system commands or import statements.
Use a Sandbox Environment
A sandbox environment is a secure execution environment that isolates and limits access to critical resources. You can use a sandbox environment to execute a user-generated equation safely without affecting other parts of your code.
Benefits of Safe String Equation Evaluation
By safely handling string equations in your Python code, you can reap several benefits, including:
Increased Security
Safe handling of string equations can prevent malicious actors from injecting harmful code into your system, stealing sensitive data or compromising system integrity.
Improved Performance
Optimizing string equation evaluation by using efficient techniques and reducing redundant calculations can improve the performance of your application or algorithm.
Better Code Quality
Handling string equations securely can lead to better code quality by reducing errors or bugs related to unexpected input or faulty expressions.
Conclusion
In conclusion, handling user-generated equations securely is essential for ensuring the safety and robustness of your Python code. Applying expert techniques like parser modules, sanitizing input, restricting keywords, and using a sandbox environment can reduce the security risks, improve performance and enhance the overall quality of your code.
| Pros | Cons |
|---|---|
| Increased security | Requires additional coding and validation steps |
| Improved performance | May limit the flexibility of user input |
| Better code quality | Requires knowledge of parser modules and input validation techniques |
The table above summarizes the pros and cons of safe string equation evaluation. While it requires additional coding and validation steps, it can significantly improve the security, performance, and quality of your Python code.
If you made it through this article, congratulations! You’re one step closer to becoming a Python pro. By now, you should have a good understanding of the different ways you can safely evaluate simple string equations. These expert techniques will come in handy when working with strings and mathematical equations in Python.
Remember to always be careful when evaluating user input, as it can potentially be malicious. The techniques outlined in this article are designed to help mitigate this risk, but it’s still important to be cautious.
If you have any questions or feedback about the content presented in this article, feel free to leave a comment below. We appreciate all feedback and are always looking for ways to improve our content. Thanks for reading!
Here are some common questions that people also ask about Python tips for safely evaluating simple string equations:
- How can I safely evaluate a simple string equation in Python?
- What are some best practices for evaluating equations with user input?
- Is it safe to use eval() for more complex equations?
- Can I evaluate equations in real-time as a user types?
- What are some common pitfalls to avoid when evaluating equations?
One expert technique is to use the built-in function eval() and pass it a restricted namespace of allowed functions and variables. This limits the potential harm from malicious input.
Always sanitize user input to prevent injection attacks, limit the scope of allowed functions and variables, and restrict the length and complexity of the input string.
No, eval() should only be used for simple equations with limited potential for harm. For more complex calculations, consider using a dedicated library or parser.
Yes, but this can be resource-intensive and may require additional security measures to prevent abuse.
Avoid using eval() without restrictions or validation, allowing unrestricted access to system resources, and trusting user input without sanitization.