Python is one of the most widely-used programming languages in the world. It is known for its simplicity, versatility, and efficiency, making it an ideal choice for programmers who want to create powerful applications with ease.
One aspect of programming that should never be overlooked is security. With cyber threats becoming more sophisticated every day, it is important to have a strong understanding of how to implement security measures in your code. That’s where Hmac-Sha1 comes in – it is a cryptographic algorithm that can help you enhance the security of your Python code.
If you’re looking for a step-by-step guide to implementing Hmac-Sha1 in your Python code, you’ve come to the right place. In this article, we will provide you with a comprehensive guide that will help you understand the basics of Hmac-Sha1 and how to use it effectively in your code.
Whether you’re a beginner or an experienced Python developer, this article is the solution to your problem. By the end of this guide, you will have a solid understanding of how to implement Hmac-Sha1 for enhanced security in your Python code. So what are you waiting for? Let’s get started!
“Implementation Hmac-Sha1 In Python” ~ bbaz
The Importance of Security in Programming
With the increasing number of cyber threats, security has become a top priority for programmers. It is essential to understand the importance of implementing strong security measures in your code to prevent data breaches and protect sensitive information.
The Basics of Hmac-Sha1 Algorithm
Hmac-Sha1 is a cryptographic algorithm used to verify the integrity and authenticity of data through a secure hash function. It is widely used in network protocols, digital signatures, and message authentication codes.
How Hmac-Sha1 Works
Hmac-Sha1 works by taking a message and a secret key, and applying a hashing algorithm to the combination of both. The output of the function is called a digest or a hash. This digest is then compared to the expected value to ensure its integrity and authenticity.
The Advantages of Using Hmac-Sha1
The use of Hmac-Sha1 provides several advantages. It is a fast and efficient method for verifying data authenticity and integrity. It also provides a high level of security since it uses a secret key that only the sender and receiver know.
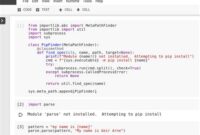
Step-by-Step Guide: How to Implement Hmac-Sha1 in Python Code
To implement Hmac-Sha1 in your Python code, follow these steps:
- Import the
hmacandhashlibmodules in your code. - Create a secret key using a random generator or a user-defined value.
- Encode your message and secret key using the
UTF-8encoding. - Apply the Hmac-Sha1 algorithm to the combination of the encoded message and secret key.
- Compare the resulting digest to the expected value to verify the authenticity and integrity of the data.
Practical Applications of Hmac-Sha1 in Python
Hmac-Sha1 algorithm can be used for a variety of practical applications such as:
- Securing password storage in databases
- Secure data transmission over networks
- Authenticating users in web applications
- Ensuring software integrity in digital signatures
Comparison: Hmac-Sha1 vs. Other Cryptographic Algorithms
There are several cryptographic algorithms available in the market. Let’s compare Hmac-Sha1 with two of the most widely used cryptographic algorithms – MD5 and SHA-256.
| Hmac-Sha1 | MD5 | SHA-256 | |
|---|---|---|---|
| Security | High | Low | Very High |
| Speed | Fast | Very Fast | Slow |
| Hash Size | 160 bits | 128 bits | 256 bits |
| Common Uses | Digital signatures, message authentication codes, web application security | Password storage, checksums | Secure data storage, digital certificates, blockchain technology |
Opinion: Why Hmac-Sha1 is a Good Choice for Python Developers
In my opinion, Hmac-Sha1 is an excellent choice for Python developers due to its simplicity, versatility, and efficiency. It is easy to implement in Python code, and its speed and security make it suitable for a wide range of applications.
While other cryptographic algorithms like SHA-256 offer higher security, their slower speed and larger hash sizes may not be suitable for all applications. Hmac-Sha1 strikes the perfect balance between security and speed, making it an ideal choice for most practical applications.
Thank you for taking the time to read this step-by-step guide on implementing Hmac-Sha1 for enhanced security in Python. We hope that the information provided has been helpful in improving your knowledge and understanding of this topic.
As we navigate through an increasingly digital world, it is crucial that we take measures to ensure the security of our online data. One such measure is the implementation of Hmac-Sha1, a strong method of data authentication that provides an extra layer of protection against malicious attacks.
If you have any further questions or concerns regarding this topic, we encourage you to seek out additional resources and continue learning about data security best practices. Thank you again for visiting our blog and we hope to provide you with more informative content in the future.
Here are some common questions that people may ask about Python Tips: Step-by-Step Guide to Implementing Hmac-Sha1 for Enhanced Security:
-
What is Hmac-Sha1?
Hmac-Sha1 is a cryptographic function that uses a secret key to create a message authentication code (MAC) for data integrity and security purposes.
-
Why is Hmac-Sha1 important for security?
Hmac-Sha1 helps ensure that data has not been tampered with or altered during transmission. It provides an additional layer of security for sensitive information.
-
How do I implement Hmac-Sha1 in Python?
You can implement Hmac-Sha1 in Python by using the built-in
hmacmodule. First, import the module and generate a secret key. Then, use thehmac.new()function to create a MAC for your data. -
What are some best practices for implementing Hmac-Sha1 in Python?
Some best practices include using a strong secret key, hashing the data before applying the HMAC function, verifying the MAC on the receiving end, and using secure communication channels.
-
Are there any alternatives to Hmac-Sha1 for data security?
Yes, there are other cryptographic functions such as Hmac-SHA256 and Hmac-SHA512 that provide stronger security measures. However, the implementation process may be more complex.